Recon Wave
Storing RSA Private keys in DNS TXT records?
To our initial surprise, hundreds of people and organisations store RSA private keys in DNS TXT records. Is that a leak, software error, some kind of misconfiguration or is there a legitimate reason? The answer might surprise you as there is a perfectly valid reason to store private keys publicly in DNS. Come along as we explore this topic.
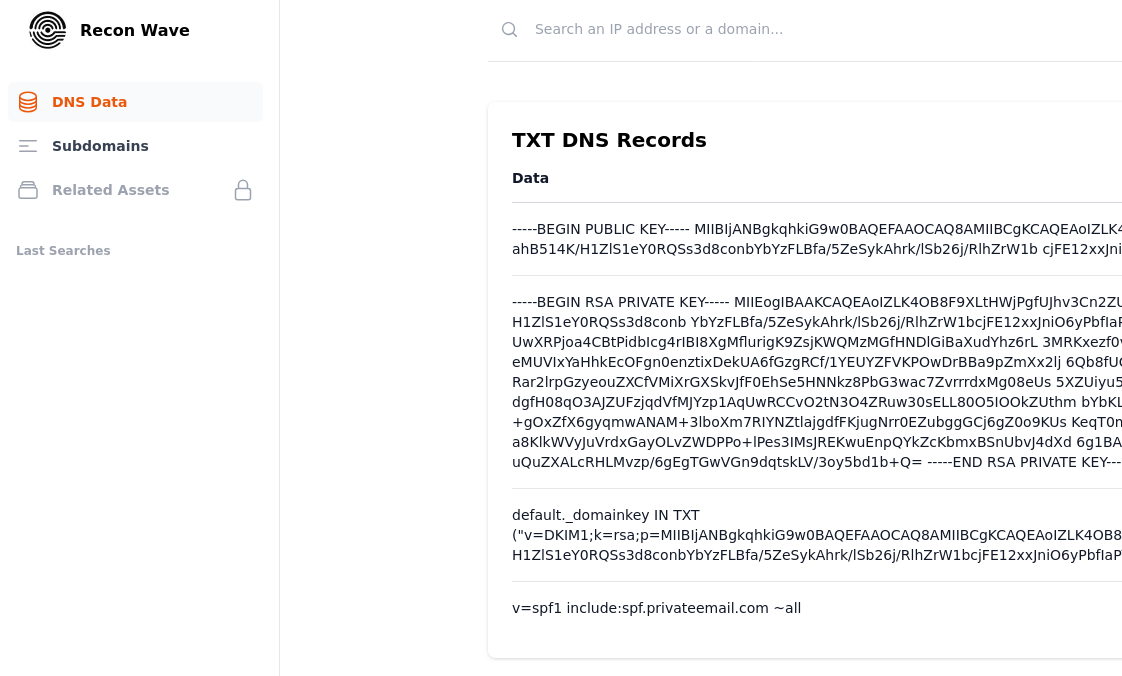
Our team has recently discovered several hundreds of RSA Private keys in TXT records of our global DNS dataset. We started acting immediately to understand what's going on and whether we should disclose the discovery to responsible personnel. To our surprise, the affected domains had nothing in common. They resolved to different IPs, were managed by different authoritative nameservers, belonged to different TLDs etc. Could all the domain owners do the same mistake?
After a long brainstorming of legitimate reasons to put private keys to DNS, we have concluded that there are none. A first principle that people learn about asymmetric cryptography is that private keys should always remain private no matter what. Publishing the secret keys is similar to publishing your passwords - it immediately undermines the integrity and security of any system or data it protects. So what are we looking at? A data leak? A misconfiguration? A software bug?
During an ongoing discussion, we have stumbled upon an article that gave us all the answers we needed and left us amazed. There is a perfectly valid reason to put private keys to DNS and it is related to DKIM.
DKIM (DomainKeys Identified Mail) is an email authentication method to verify sender of an email. The sender adds a unique digital signature in the email headers, which recipients' mail servers can verify using the public key published in the sender's DNS records. This process ensures that the message was not altered during transit and that it legitimately originated from the claimed domain, helping to prevent email spoofing and phishing attacks.
DKIM successfully fulfills its goal of reducing email-based fraud, such as phishing and spoofing. However, the side effect is that anyone can cryptographically verify authenticity of email even many years after it was sent - including leaked or stolen emails. If an organisation wants to prevent that, it can rotate DKIM keys and release the old secret keys. This way, any future email with valid signature can be denied as a forgery which gives the organisation a plausible deniability.
We are relieved that hundreds of organisations did not leak their private keys by accident. Feel free to browse our DNS dataset using our free web-interface available at search.reconwave.com to discover more interesting findings or records of your organisation.
Organisations usually forget all the assets they own which attackers take advantage of. In case you want to have your attack surface under control, get in touch with us at Recon Wave to prevent future cybersecurity incidents.
We hope you've learned something new—as we did—since it was difficult for us to find any relevant information about this topic online. Don't forget to follow us on X or LinkedIn to stay up-to-date with all the news and other upcoming blogposts.
Be safe and ride the Recon Wave with us! 🌊