State of Global DNS - part 1
The Alarming Prevalence of Zone Transfers
DNS is a cornerstone of today’s internet, making its security absolutely critical. In this blog series, we’ll dive into the global state of DNS from the security perspective, leveraging our extensive dataset to uncover key trends and risks. In this first part, we’ll focus on zone transfers — a fundamental yet often overlooked aspect of DNS management. We found that 8% of all nameservers still have zone transfers enabled for all authorized zones, potentially exposing sensitive information to malicious actors.
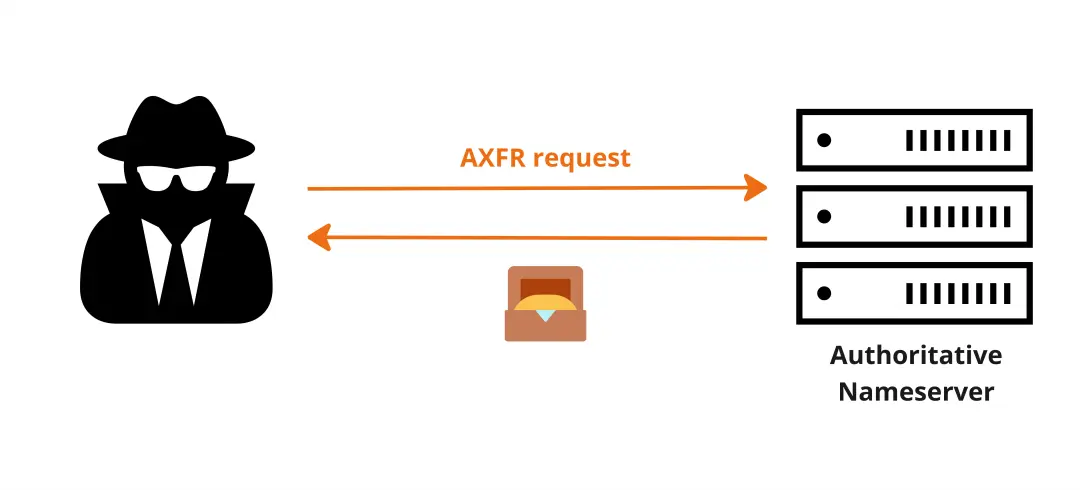
Zone transfer is a DNS mechanism to replicate DNS records from one nameserver to another, ensuring redundancy and consistency across the domain's DNS infrastructure. DNS zone transfers are crucial for maintaining consistent DNS data across multiple servers. There are two types of zone transfers: AXFR (full zone transfer) and IXFR (incremental zone transfer). In this post, we’ll focus exclusively on AXFR, where the response contains all DNS records for the specified zone.
As an example, let’s use the zone dig:
> domain=zonetransfer.me; dig axfr $domain @$(dig $domain ns +short | head -n1)
; <<>> DiG 9.18.24-1-Debian <<>> axfr @nsztm1.digi.ninja zonetransfer.me
; (1 server found)
;; global options: +cmd
zonetransfer.me. 7200 IN SOA nsztm1.digi.ninja. robin.digi.ninja. 2019100801 172800 900 1209600 3600
zonetransfer.me. 300 IN HINFO "Casio fx-700G" "Windows XP"
zonetransfer.me. 301 IN TXT "google-site-verification=tyP28J7JAUHA9fw2sHXMgcCC0I6XBmmoVi04VlMewxA"
zonetransfer.me. 7200 IN MX 0 ASPMX.L.GOOGLE.COM.
zonetransfer.me. 7200 IN MX 10 ALT1.ASPMX.L.GOOGLE.COM.
zonetransfer.me. 7200 IN MX 10 ALT2.ASPMX.L.GOOGLE.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX2.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX3.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX4.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN MX 20 ASPMX5.GOOGLEMAIL.COM.
zonetransfer.me. 7200 IN A 5.196.105.14
zonetransfer.me. 7200 IN NS nsztm1.digi.ninja.
zonetransfer.me. 7200 IN NS nsztm2.digi.ninja.
_acme-challenge.zonetransfer.me. 301 IN TXT "6Oa05hbUJ9xSsvYy7pApQvwCUSSGgxvrbdizjePEsZI"
_sip._tcp.zonetransfer.me. 14000 IN SRV 0 0 5060 www.zonetransfer.me.
14.105.196.5.IN-ADDR.ARPA.zonetransfer.me. 7200 IN PTR www.zonetransfer.me.
asfdbauthdns.zonetransfer.me. 7900 IN AFSDB 1 asfdbbox.zonetransfer.me.
...
Note: to check your own domain, exchange zonetransfer.me with your domain in the command above
While essential for maintaining synchronization between primary and secondary DNS servers, zone transfers can inadvertently expose sensitive information that malicious actors could exploit to learn more about a zone's structure. To prevent this, zone transfers should be restricted to authorized users only. This is typically done by whitelisting the IP addresses of secondary nameservers.
Even though the general consensus is that publicly open zone transfers pose a security risk, there are large zones that intentionally allow public zone transfers. One example is the
We build Recon Wave on top of a massive global OSINT dataset, which includes DNS records. Our dataset contains around
To our surprise, 8.2% of all nameservers have zone transfers enabled. While this number seems alarming at first, it's important to consider the total number of domains these nameservers manage. With the modern internet becoming more centralized, the majority of domains are handled by major providers like Cloudflare, Amazon, and others. These 8.2% of nameservers are responsible for only 0.4% of the domains in our dataset. Although this percentage is lower, we're still talking about millions of domains.
In the next two charts, we show the top 10 TLDs with the most affected APEX domains and nameservers. Unsurprisingly,
It’s also interesting to see which TLDs have the highest percentage of nameservers with zone transfers enabled. Leading the stats is Russia, with an astonishing 21.8%. In second place is the
The total number of nameservers with zone transfers enabled surprised us, and we definitely hoped the number would be smaller. We will continue sharing more interesting facts about the current state of global DNS, so make sure to follow us on X or LinkedIn to stay updated with all the latest news and upcoming blog posts.
If you wish to have your DNS infrastructure secured and actively monitored, explore Recon Wave Platform or reach out to us!
Be safe and ride the Recon Wave with us! 🌊